The U.S. Federal Communications Commission, in taking the first step toward creating Net neutrality rules in 2009, has reignited a contentious debate about government regulation of the Internet.
Opponents of new Net neutrality rules argue that an FCC proposal released in October would create intrusive new rules for the Internet and would mark a major shift in the U.S. government's generally hands-off approach to Web regulation. The FCC's proposed Net neutrality rules would, among other things, require Internet service providers to "treat lawful content, applications, and services in a nondiscriminatory manner."
New rules aren't needed, because there have been few examples of broadband providers blocking or slowing Web content and applications, critics said. "Where's the beef?" Barbara Esbin, a senior fellow with the free-market think tank Progress and Freedom Foundation (PFF), wrote in a paper published this month. "There is little or no evidence that broadband ISPs are plotting to alter the fundamental attributes of the Internet in such nefarious ways or of actual consumer harms from today's broadband network management practices."
The PFF and other critics say Net neutrality rules will hamper broadband providers' investment in their networks, by creating rules on how they can use those investments. The Net neutrality rules could prohibit innovative, new business models focused on tiered pricing or specialized networks, critics have said.
Backers of Net neutrality rules say the FCC's proposal would simply reinstate old rules, relaxed by the FCC in 2005, that required traditional telecom carriers to share their networks. Rules are needed because there have already been examples of ISPs blocking or slowing Web content, they say, including Comcast's attempts in 2007 and 2008 to slow BitTorrent peer-to-peer traffic in the name of fighting network congestion.
"Please keep the Internet business neutral, I am tired of hearing A&T and other businesses saying they are being hurt by Net neutrality," Internet user Hawk Bailey of New Baltimore, Michigan, wrote in comments filed with the FCC. "Instead, they want to earn extra money and power by allowing companies to pay for priority access and requiring individuals and small businesses to do the same to compete."
The debate over whether the FCC or U.S. Congress should create Net neutrality rules has been simmering in Washington, D.C., for the better part of the decade. In 2005, the FCC ended requirements that traditional telecom carriers share their networks with competitors, and Net neutrality advocates renewed their arguments that Net neutrality rules were needed to protect consumers in a broadband market without many competitors.
But Democrats in Congress were unable to push through a Net neutrality law, and the Republican-controlled FCC was unwilling to act. But President Barack Obama said during 2008's presidential campaign that Net neutrality rules were one of his top tech priorities, and Obama-appointed FCC Chairman Julius Genachowski pushed forward with a Net neutrality rulemaking proceeding this year.
While activists on the far sides of the Net neutrality debate have continued their rhetorical battles in recent weeks, some of the major companies involved in the issue have seemed to soften their stances. In October, the chief executives of Google, a major Net neutrality advocate, and broadband provider Verizon Wireless co-authored a statement on finding common ground in the Net neutrality debate.
"It's essential that the Internet remains an unrestricted and open platform," both companies said.
And AT&T, one of the most vocal opponents of Net neutrality rules, said this month that "preserving the open character of the Internet is critically important to ensuring that all consumers have the opportunity to be creators of content and innovators from their homes or their garages."
Net neutrality supporters, however, suggested AT&T's position hadn't changed that much, with the company still suggested the FCC shouldn't prohibit broadband providers from entering into commercial agreements in which they provide "value-added" broadband services to some Internet companies
Some opponents suggested now isn't the time for the FCC to create Net neutrality rules as the agency is also preparing a national broadband plan focused on getting more U.S. residents access to broadband service. Congress required the FCC to create the national broadband plan in a huge economic stimulus package passed early in 2009.
Net neutrality rules seem at odds with expanding broadband access to more U.S. residents, argued Esbin and other critics.
"The primary question that one should ask before embarking on a new regulatory regime is, 'will this help achieve the consensus goal of bringing affordable broadband service to all the people of America?'" she wrote. "Surely the goal will be made harder by imposing new regulatory constraints on the ability of broadband ISPs to provide service, manage their networks, and develop new business models as the needs of end users and Internet content, applications, and service providers change over time."
Many older U.S. residents are concerned about Net neutrality rules, added Bruce Yampolsky, president of the Missouri Silver Haired Legislature, a seniors advocacy group. "The FCC's actions relating to Net neutrality could have a profound impact on our constituency's ability to access and adopt broadband Internet, creating yet another barrier for us to overcome," he wrote in a filing with the FCC. "We feel that your actions regarding Net neutrality are misplaced given the state of broadband access and affordability in the United States."
Net neutrality rules could create "onerous burdens" on ISPs even as the elderly and other groups of U.S. residents have low broadband adoption rates, Yampolsky wrote.
Others argue that new Net neutrality rules will give consumers control of their own broadband experiences and allow freedom of speech.
"Net neutrality is what our country needs," Sheldon Peck, an Internet user from Newton, Massachusetts, wrote in a filing to the FCC. "Please DO NOT listen to special interest groups ... who are paid off by industry. Let's finally take back the airwaves for the citizens. It will re-empower this great, free country."
Read More ..

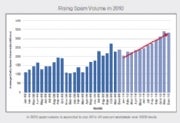 Social networking isn't just for kids anymore. Since businesses and organizations began digging into the gambit of cyber friends and fans, spammers have taken the opportunity to ramp up efforts to grab the attention of the unsuspecting. Facebook claims that site visitations increased 105 percent from December 2008 to December 2009. (Click on the chart for a close-up view.)With these kinds of numbers, it's no wonder spamming has followed suit.
Social networking isn't just for kids anymore. Since businesses and organizations began digging into the gambit of cyber friends and fans, spammers have taken the opportunity to ramp up efforts to grab the attention of the unsuspecting. Facebook claims that site visitations increased 105 percent from December 2008 to December 2009. (Click on the chart for a close-up view.)With these kinds of numbers, it's no wonder spamming has followed suit. mpty wallets. "Facebook has also been used to launch '419' scams. The scam normally starts when a Facebook user is fooled into handing over Facebook login credentials, or has their login credentials stolen by keylogger malware on their machine. With these stolen credentials, the criminal logs in to the user's Facebook account and sends messages to the user's Facebook friends, asking them to wire money -- supposedly because the user is stranded in a foreign country," the Honeypot report says.
mpty wallets. "Facebook has also been used to launch '419' scams. The scam normally starts when a Facebook user is fooled into handing over Facebook login credentials, or has their login credentials stolen by keylogger malware on their machine. With these stolen credentials, the criminal logs in to the user's Facebook account and sends messages to the user's Facebook friends, asking them to wire money -- supposedly because the user is stranded in a foreign country," the Honeypot report says.

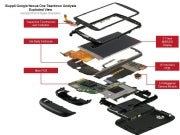
 The Nexus is raising quite the ruckus. From the
The Nexus is raising quite the ruckus. From the